Configure Istio Ingress Gateway
Until now, you used a Kubernetes Ingress to access your application from the outside. In this module, you configure the traffic to enter through an Istio ingress gateway, in order to apply Istio control on traffic to your microservices.
Store the name of your namespace in the
NAMESPACEenvironment variable. You will need it to recognize your microservices in the logs:$ export NAMESPACE=$(kubectl config view -o jsonpath="{.contexts[?(@.name == \"$(kubectl config current-context)\")].context.namespace}") $ echo $NAMESPACE tutorialCreate an environment variable for the hostname of the Istio ingress gateway:
$ export MY_INGRESS_GATEWAY_HOST=istio.$NAMESPACE.bookinfo.com $ echo $MY_INGRESS_GATEWAY_HOST istio.tutorial.bookinfo.comConfigure an Istio ingress gateway:
$ kubectl apply -f - <<EOF apiVersion: networking.istio.io/v1 kind: Gateway metadata: name: bookinfo-gateway spec: selector: istio: ingressgateway # use Istio default gateway implementation servers: - port: number: 80 name: http protocol: HTTP hosts: - $MY_INGRESS_GATEWAY_HOST --- apiVersion: networking.istio.io/v1 kind: VirtualService metadata: name: bookinfo spec: hosts: - $MY_INGRESS_GATEWAY_HOST gateways: - bookinfo-gateway.$NAMESPACE.svc.cluster.local http: - match: - uri: exact: /productpage - uri: exact: /login - uri: exact: /logout - uri: prefix: /static route: - destination: host: productpage port: number: 9080 EOFSet
INGRESS_HOSTandINGRESS_PORTusing the instructions in the Determining the Ingress IP and ports section.Add the output of this command to your
/etc/hostsfile:$ echo $INGRESS_HOST $MY_INGRESS_GATEWAY_HOSTAccess the application’s home page from the command line:
$ curl -s $MY_INGRESS_GATEWAY_HOST:$INGRESS_PORT/productpage | grep -o "<title>.*</title>" <title>Simple Bookstore App</title>Paste the output of the following command in your browser address bar:
$ echo http://$MY_INGRESS_GATEWAY_HOST:$INGRESS_PORT/productpageSimulate real-world user traffic to your application by setting an infinite loop in a new terminal window:
$ while :; do curl -s <output of the previous command> | grep -o "<title>.*</title>"; sleep 1; done <title>Simple Bookstore App</title> <title>Simple Bookstore App</title> <title>Simple Bookstore App</title> <title>Simple Bookstore App</title> ...Check the graph of your namespace in the Kiali console
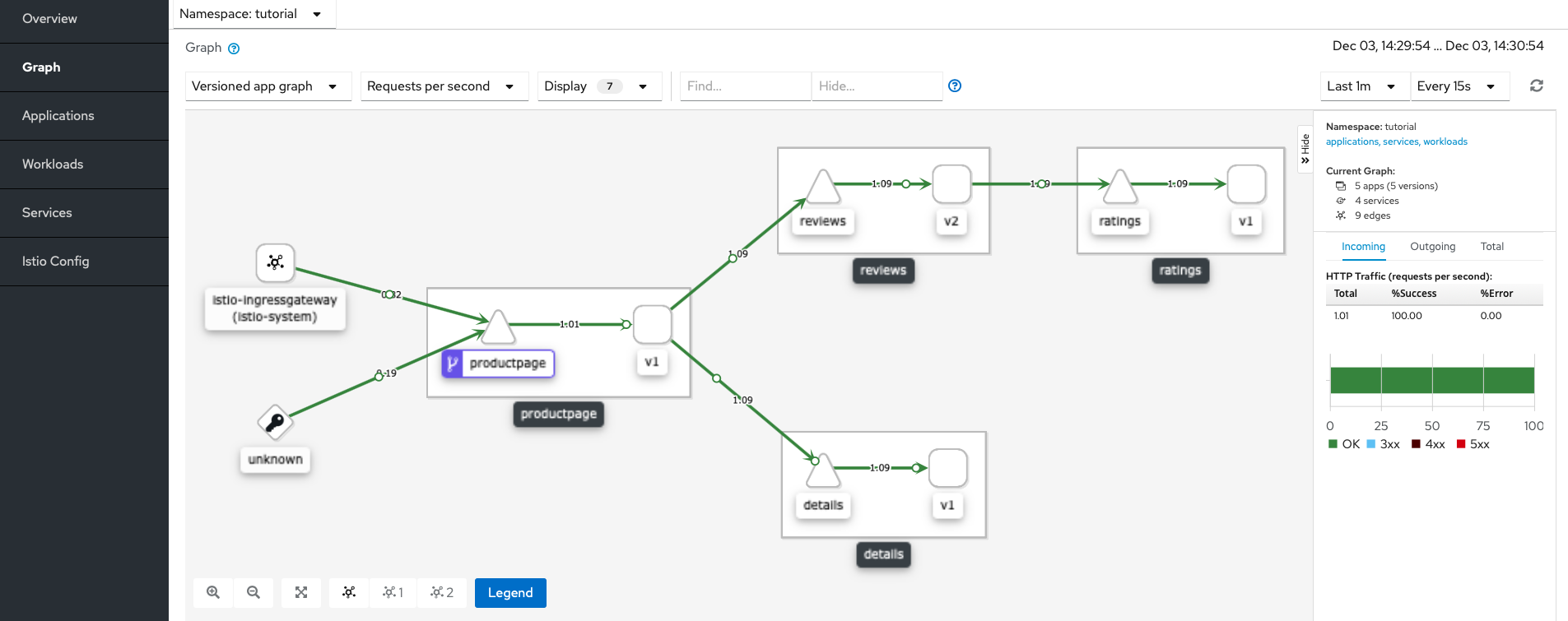
my-kiali.io/kiali/console. (Themy-kiali.ioURL should be in your/etc/hostsfile that you set previously).This time, you can see that traffic arrives from two sources,
unknown(the Kubernetes Ingress) and fromistio-ingressgateway istio-system(the Istio Ingress Gateway).Kiali Graph Tab with Istio Ingress Gateway At this point you can stop sending requests through the Kubernetes Ingress and use Istio Ingress Gateway only. Stop the infinite loop (
Ctrl-Cin the terminal window) you set in the previous steps. In a real production environment, you would update the DNS entry of your application to contain the IP of Istio ingress gateway or configure your external Load Balancer.Delete the Kubernetes Ingress resource:
$ kubectl delete ingress bookinfo ingress.extensions "bookinfo" deletedIn a new terminal window, restart the real-world user traffic simulation as described in the previous steps.
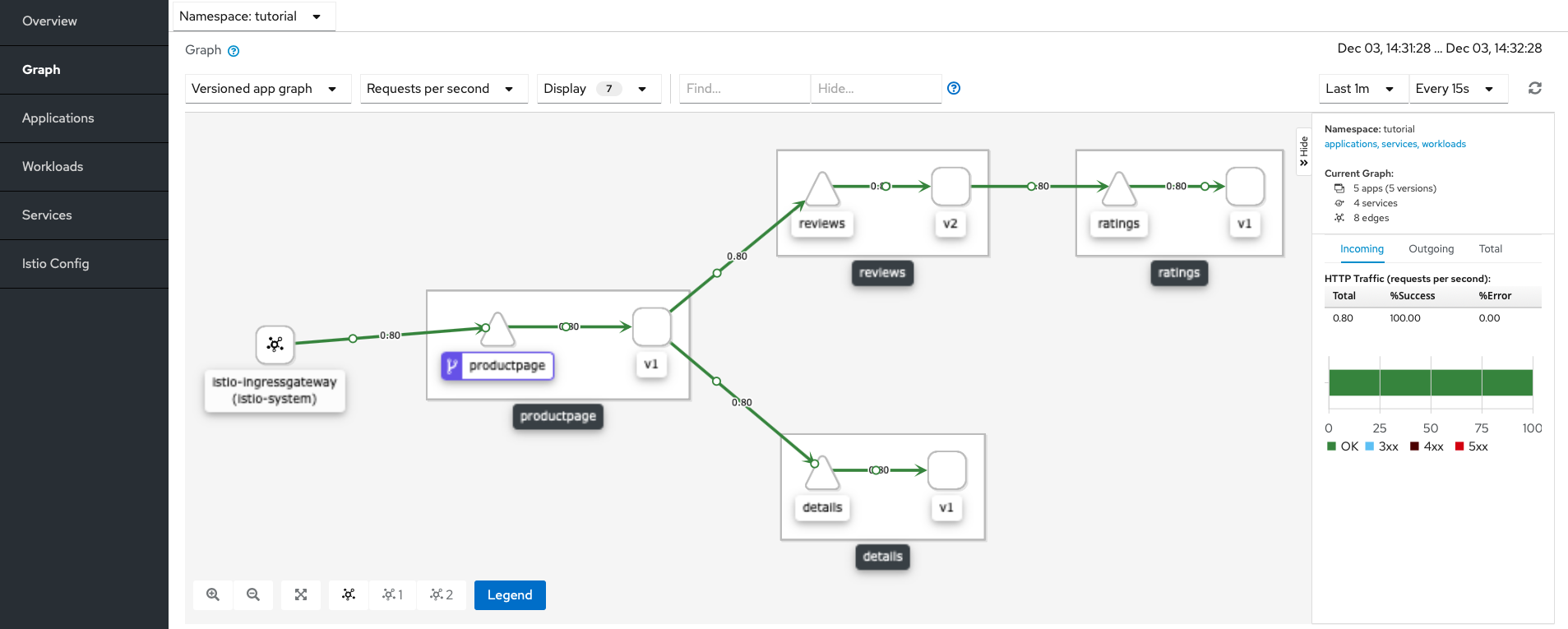
Check your graph in the Kiali console. After about a minute, you will see the Istio Ingress Gateway as a single source of traffic for your application.
Kiali Graph Tab with Istio Ingress Gateway as a single source of traffic
You are ready to configure logging with Istio.